For those already consuming Microsoft Office 365, then you will undoubtedly (to some level) be utilising Azure Active Directory. Azure AD comes with an array of tools, some of which aren’t confined to public cloud; some can even aid and strengthen your on-premises applications. One such tool is the Azure Multi-Factor Authentication Server, an on-premises 2-factor authentication mechanism which can integrate with on-prem VMware Horizon environments.
The Azure MFA Server enables us to further enhance the security of numerous applications capable of integrating with 2FA authentication, and VMware Horizon has been able to integrate with such solutions for some time. This additional level of security is a much sought after function which serves to further secure public access to internal desktop pools.
Having utilised a number of 2FA provider services over the years, it can be tricky to pick the right one, more so as the wrong choice will likely lock you in to the product of choice for X years. All come at an additional cost, and some can have limited management functionality. The Azure Multi-Factor Authentication Server is simple to deploy and configure, and if you already utilise Azure Active Directory Premium, Enterprise Mobility Suite, or Enterprise Cloud Suite licensing, you are already paying for the functionality. So why not consume it?
Note: This article assumes you a) already utilise Azure AD (and are licensed accordingly), b) have deployed and configured the Microsoft Azure Multi-Factor Authentication Server to authenticate against a Windows domain, and c) users have registered with the MFA Server. Likewise, this article also assumes your domain users have registered their mobile devices and have the Microsoft Authenticator app installed. This article will not cover the installation or configuration of the Microsoft Azure Multi-Factor Authentication Server, however, full details for these areas can be viewed via Microsoft’s Getting started with the Azure Multi-Factor Authentication Server.
Procedure
As mentioned above, configuring the Azure MFA Server and VMware Horizon is nice and quick, and can be covered in four simple steps.
- Enable RADIUS authentication on the Microsoft Multi-Factor Authentication Server
- Add VMware Horizon Connection Servers as RADIUS Clients
- Configure VMware Horizon Connection Servers to utilise the Microsoft MFA Server for 2-Factor Authentication
- Test remote access.
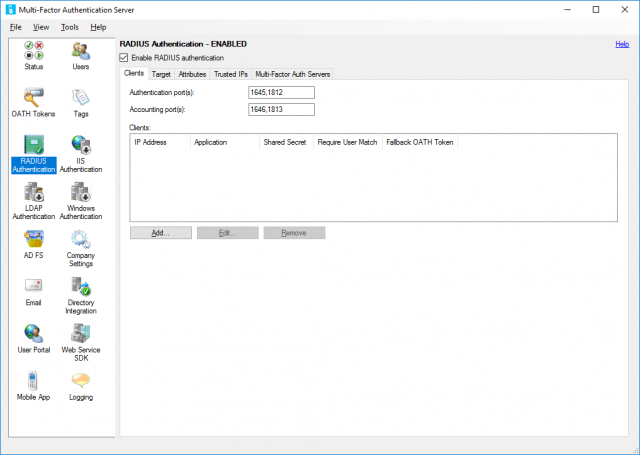
1. Launch the Multi-Factor Authentication Server application. Browse to RADIUS Authentication > Clients, and check the Enable RADIUS Authentication tick box. Next, click Add….
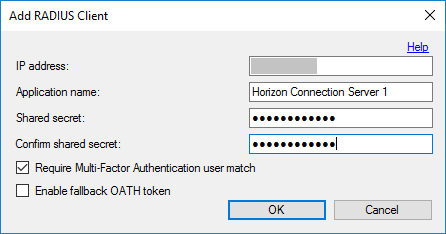
2. Add all VMware Horizon Connection Servers and configure accordingly. Ensure you make note of the Shared secret. You will need this in a later step.
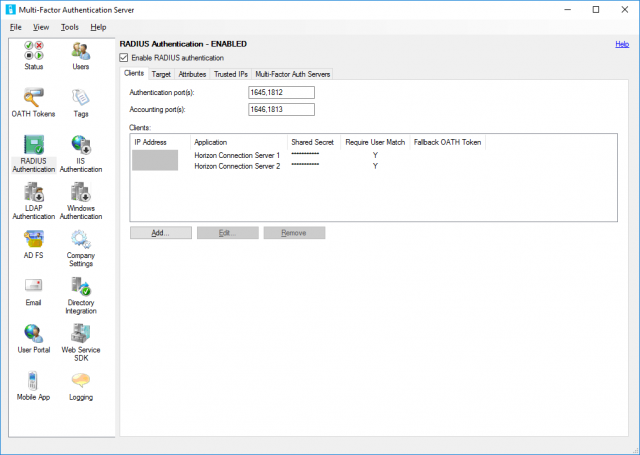
3. Confirm successful addition of all VMware Horizon Connection Servers.
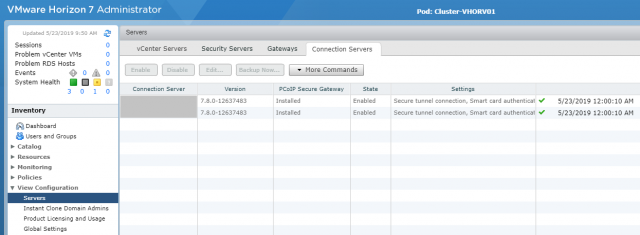
4. Login to the VMware Horizon Administrator console and browse to View Configuration > Servers > Connections Servers. Select one of your Horizon View Connection Servers and click Edit.
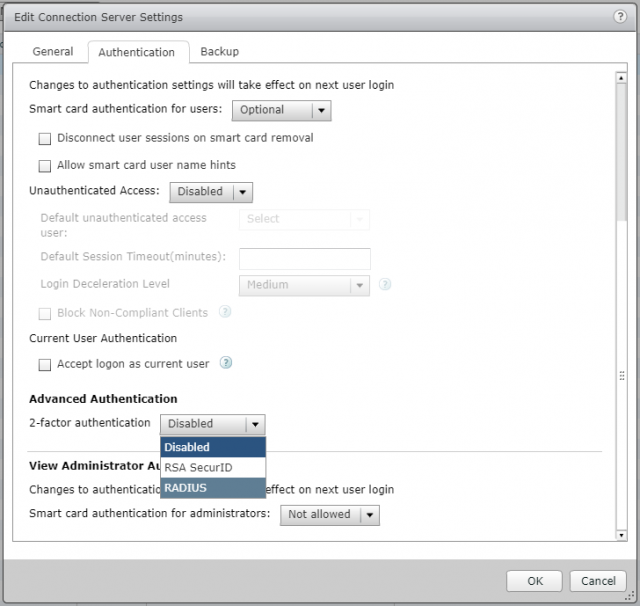
5. Browse to the Authentication tab and set 2-Factor Authentication to RADIUS.
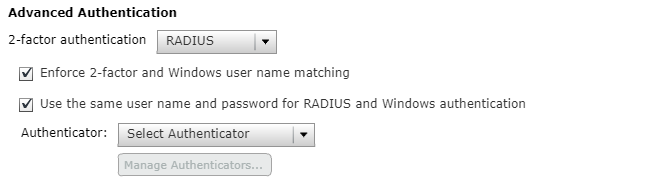
6. Ensure both Enforce 2-factor and Windows user name matching and Use the same user name and password for RADIUS and Windows authentication are checked.
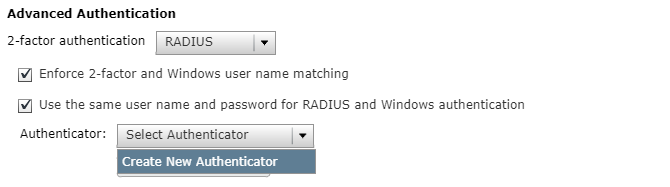
7. From the Authenticator field, select Create New Authenticator.
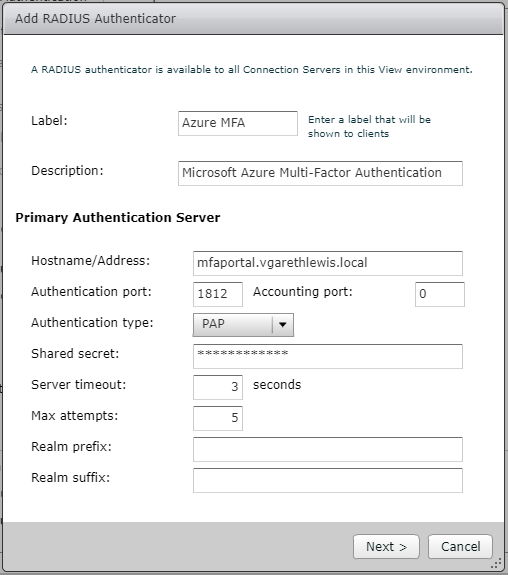
8. Configure the new RADIUS Authenticator with the Azure MFA Server FQDN (consider whether this solution is load-balanced or standalone, etc.) and add the Shared Secret which we created in Step 2. When ready, click Next.
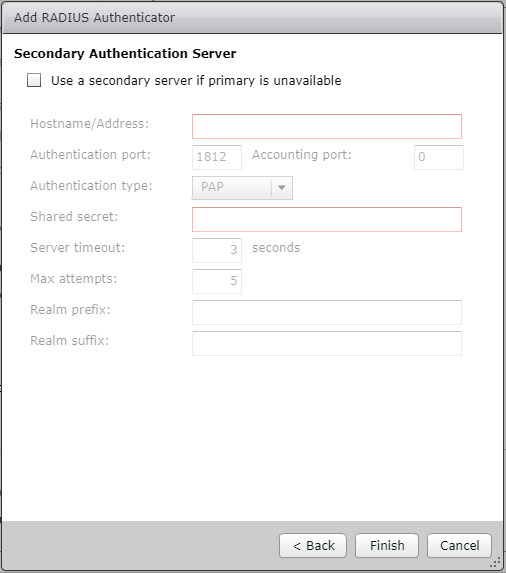
9. On the Secondary Authentication Server page, accept the defaults, and click Finish.
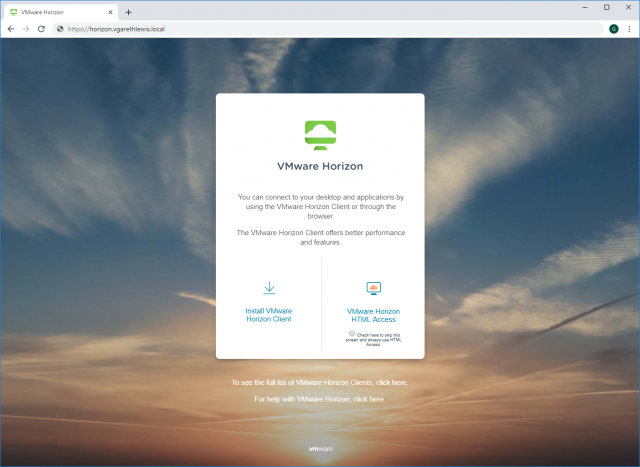
10. Finally, let’s test. Browse to the public facing FQDN for your VMware Horizon environment and click VMware Horizon HTML Access.
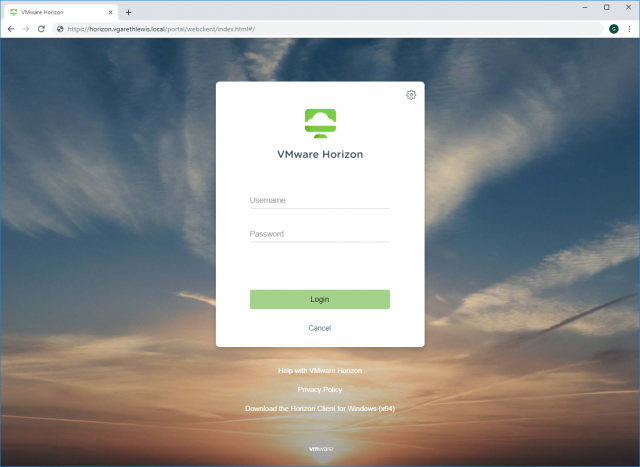
11. Enter your domain credentials and click Login.
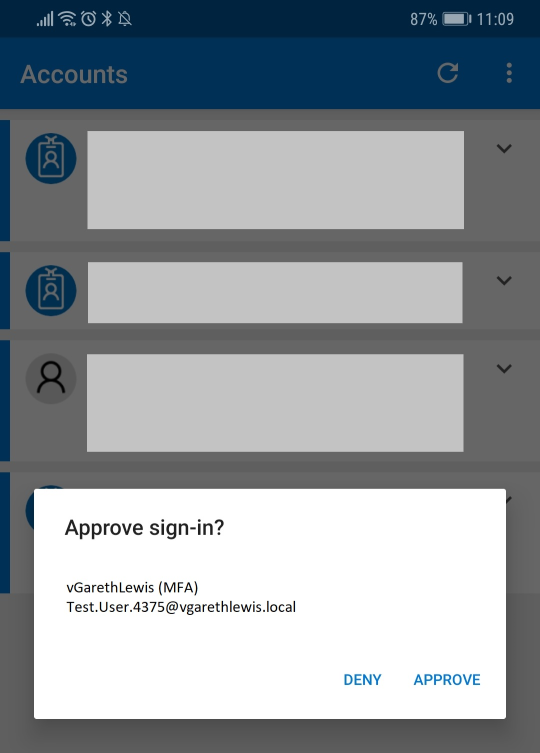
12. On your registered mobile device, note the pop-up, and click Approve.
13. Once approved, you will be passed through to the VMware Horizon launch dashboard.
This concludes the process of integrating VMware Horizon with the Azure Multi-Factor Authentication Server.

Do I have to repeat the same setup on all my connection servers?
Just the one Lorenze. The configuration will then apply to all peered connection servers.
Great article. Thank you for this break down! I have a question. Would all active users need to be logged out for this to work. If not, what is the impact if you have users logged in? Im trying to figure out how to best get this implemented in live horizon environments.
Hey David,
The process wouldn’t affect active users, only those that logon after enabling MFA.
When implementing this in the past I’ve worked with the customer to ensure clear comms are sent to all users before MFA is enabled; the reason being is that those utilising the service will need to register a mobile device with the MFA Servers prior to the service being enabled.
This is more a communication/management piece than that of a technical one. All of the configuration can be done in the background and during an our-of-hours testing window. Once you’re happy, it’s time for comms and a go-live date.
Hope that helps!
In our environment, we have external connection servers bound to security servers. We also have internal connection servers. Two different vips on the f5 depending on your source connection. Can MFA be set up to just force external connected users to MFA, or is this an all or nothing configuration?
Thanks for your assistance in advance!.
Any updates to integrate with cloud-based Azure Multi-Factor Authentication? MFA Server is no longer offered from MS. Thanks!
Hi Patrick, no plans to investigate this at the moment I’m afraid, but I will be diving into VMware Identity Manager at some point. Stay tuned
I am also curious if it’s possible to set up the Azure cloud MFA with Horizon. Microsoft does still have MFA Server, but it only supports tokens or SMS at this point
Hi Max, no plans to investigate this at the moment I’m afraid, but I will be diving into VMware Identity Manager at some point. Stay tuned
Has there been anyone that has set this up with Azure ad Cloud MFA yet? I can’t believe that nobody has done this yet.
Hi Cory, I’d hope so by now. I moved companies since this post, so I no longer have much/any exposure to Azure I’m afraid. A good opportunity for someone out there to write a nice follow-up blog post 🙂
Hi Gareth,
Is there a way to avoid using PAP?
Hey Alex, apologies, I’ve not worked with any Azure elements since last June, so I’m a little out of the loop as to what’s possible. A lot of people seem to be using Azure-based MFA in conjunction with Horizon now; however, I’m also seeing a lot of folks using VMware Identity Manager. I suppose it depends on your current consumption level of Azure, etc. Apologies for the vague reply, however, I’m fully VMware focused these days so I wouldn’t want to advise you incorrectly.
Just looking for clarification. It looks like it will only support one method? We currently have everyone using RSA and we want to move to MSFT authenticator. I want to know if the migration would need to happen in a big bang or we can migrate groups.
Hi Norman,
This post takes me back. Apologies in advance Norman, I’ve not worked with this since it was posted. I foresee this would need to be a big bang approach. Once you have a) added your Connection Servers to the MFA Server, and b) switched the authentication method of your Connection Servers, all users would be required to approve via an authenticator app. As such, you’d need all users to be registered for MFA, for example, prior to this work taking place. From memory, this was the biggest time consumer and was more a communication process than a technical one.