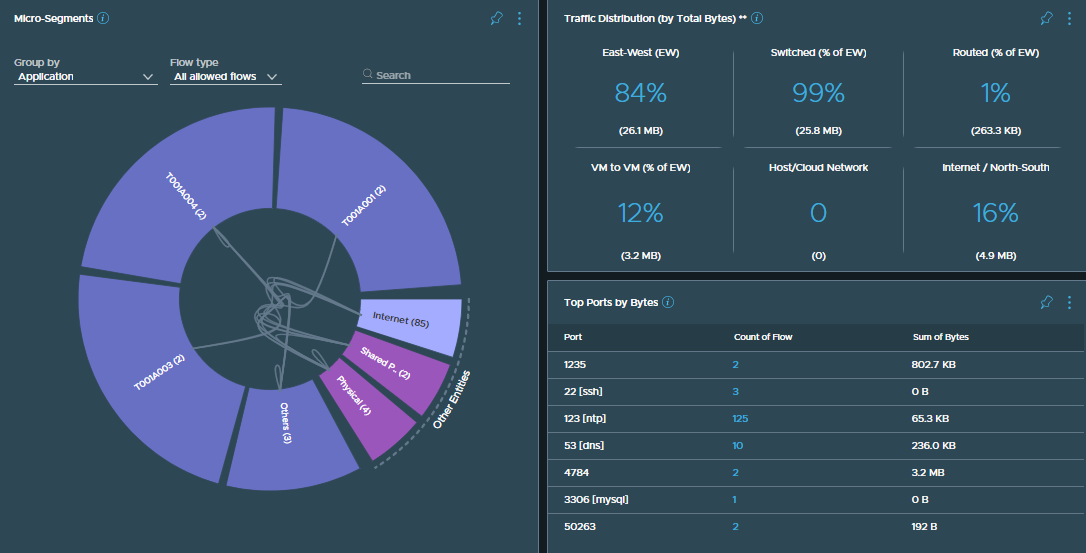
VMware NSX Distributed Firewall (DFW) FQDN Filtering
I recently had a great VMware NSX discussion with a contact on Twitter. They had reached out to me wondering if there was a way of restricting a VM’s connectivity to the internet by limiting its access to a set of wildcard addresses, e.g. *.example.com. The specific ask was to restrict access to Microsoft Windows Server Update Services, as the vast list of underlying IP addresses for *update.microsoft.com, *.download.windowsupdate.com, etc., changes regularly. In this scenario, utilising wildcards within the VMware NSX DFW rules would be hugely advantageous.
FQDN filtering within VMware NSX has been available for some time and is a quick and easy task to configure, either to allow or restrict traffic. In this article, we look at the process of implementing FQDN filtering and validate post-implementation.
Continue reading → VMware NSX Distributed Firewall (DFW) FQDN Filtering