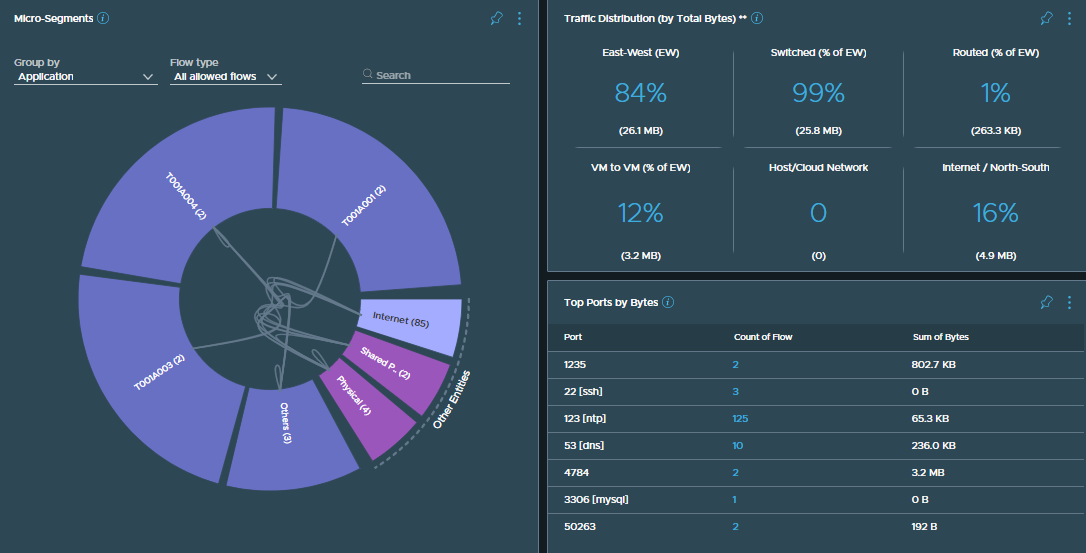
VMware NSX Micro-Segmentation Only Deployment
When we talk about VMware NSX (formerly VMware NSX-T Data Center), most of us think about abstracting management of the network away from the physical fabric thanks to NSX’s magic sauce and overlay networking capability via Geneve encapsulation. However, overlay networking isn’t always the primary use case, with a high volume of customers opting for micro-segmentation only.
Some customers, for example, are happy to allow the network’s management and physical gateways to remain within the physical fabric. Perhaps their organisation already has an alternative software-defined networking product, or they simply don’t make that many changes within their network. So, how can customers use micro-segmentation via the NSX Distributed Firewall (DFW)? Simply put, by utilising currently existing vSphere environments and VDSs in conjunction with the NSX DFW.
Continue reading → VMware NSX Micro-Segmentation Only Deployment